How to Verify Image Authenticity Online: A Comprehensive Guide by Tophinhanhdep.com
The digital realm teems with a vast array of visual content, from stunning nature wallpapers and intricate abstract art to emotionally resonant backgrounds and meticulously curated aesthetic collections. At Tophinhanhdep.com, we are dedicated to providing high-quality images and insights into photography, visual design, and creative inspiration. Yet, the sheer volume and accessibility of digital imagery also introduce a critical challenge: ensuring authenticity. In an era where advanced photo manipulation and sophisticated AI-generated content are increasingly prevalent, discerning genuine visuals from fabricated ones has become paramount. Unethical activities, ranging from online scams and identity theft to the widespread dissemination of fake news, often hinge on doctored images designed to mislead and defraud. This guide, presented by Tophinhanhdep.com, will equip you with effective strategies and essential tools to navigate the complexities of online image verification, helping you protect yourself from visual deception and uphold the integrity of the images you encounter.
The Evolving Landscape of Digital Image Deception

The ease with which images can be altered, reproduced, and shared across the internet has fundamentally reshaped our trust in visual information. What once demanded specialized skills in photo manipulation now often requires only a few clicks or a simple text prompt. This accessibility, while fostering incredible creativity in digital art and photo manipulation, also inadvertently cultivates an environment ripe for misinformation and fraudulent activities.
From Photoshop to Deepfakes: The Rise of Synthetic Imagery
The past few years have witnessed an unprecedented surge in generative artificial intelligence (AI), elevating image fakery to a whole new level. Beyond traditional Photoshop edits—where elements might be cropped, composited, or color-corrected—AI can now create hyper-realistic images that are entirely synthetic, making them extraordinarily difficult to differentiate from genuine photographs. The viral sensation of the Pope in a white designer puffer jacket in 2023 stands as a potent reminder of AI’s burgeoning capabilities. As AI technology continues its rapid advancement, we anticipate an even greater proliferation of convincing fake images and videos. This phenomenon directly impacts “Image Inspiration & Collections,” as trending styles can be manufactured rather than organically captured or genuinely photographed. Fraudsters readily exploit these advancements to create fake profiles for “catfishing,” promote shady schemes with celebrity likenesses, or even engineer deepfake video and audio to mimic authority figures for large-scale scams.
Beyond Simple Photo Manipulation
Even as AI pushes the boundaries of fakery, simpler forms of image manipulation remain widespread and equally deceptive. These often involve repurposing real photographs from one event to misrepresent another or subtly altering details within an existing image. For instance, a high-resolution photograph (a cornerstone of Tophinhanhdep.com’s offerings) might be entirely genuine but used in a misleading context, compromising its authenticity from a narrative standpoint. The proliferation of such manipulated content underscores the importance of critical visual literacy. It’s crucial to understand how various “editing styles” in “digital photography” can be applied for both legitimate artistic expression and malicious distortion.

Core Strategies for Image Verification
When confronted with an image that raises suspicion, a methodical approach to verification is crucial. Rather than relying solely on gut feeling, employing established methodologies can significantly improve your ability to uncover the truth. Tophinhanhdep.com advocates for a multi-pronged strategy that begins with contextual analysis and progresses to technical scrutiny.
Investigating the Image’s Source and Context
The initial and often most critical step in verifying an image’s authenticity is to meticulously scrutinize its origin. If you encounter a picture on any social media platform or website, immediately assess the credibility of the source. An image featured on an untrustworthy site, a social media profile with a limited history, or one known for disseminating sensational or unverified content is inherently more likely to be fake.
To properly evaluate the source:
- Social Media Profile Examination: Review the account’s previous posts and activity. Has this profile a history of sharing manipulated images or engaging in suspicious behavior? The comments section of posts can also offer valuable insights into how other users perceive the account’s reliability.
- Website Reputation Assessment: If the image appears on a website, investigate the site’s overall reputation. Are its other articles and pages known for featuring authentic visuals and credible information? A thorough investigation of the site’s history and content quality can often provide strong clues about the image’s veracity.
- Narrative Consistency Check: Does the image’s caption or accompanying text align with what reputable news outlets or official sources are reporting about the subject or event? A significant change in context across different sources, or a sensationalized narrative, can strongly indicate inaccuracy or deliberate manipulation. Even a “beautiful photography” piece can be miscaptioned to spread misinformation.
Uncovering Origins with Reverse Image Search
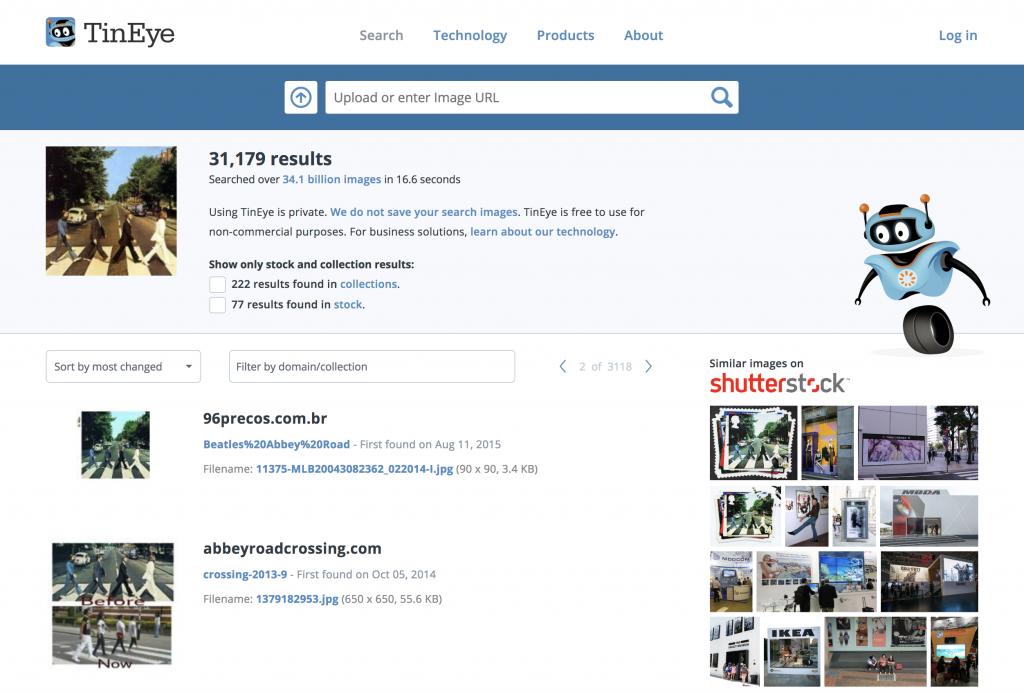
One of the most potent and widely accessible techniques for image verification is the reverse image search. This powerful method allows you to upload a suspicious picture to a specialized tool, which then scans the internet for identical or visually similar images. By comparing the image in question with its variants from diverse sources, you can conduct a comparative and contextual analysis that frequently exposes inconsistencies.
Several reliable reverse image search tools are available and recommended by Tophinhanhdep.com:
- Google Search by Image: This widely used tool allows you to upload an image or provide its URL to swiftly discover its original source and track other instances of its publication. It also suggests visually similar images, which can be invaluable for identifying edited versions.
- TinEye: Another highly effective reverse image search engine that excels at tracking the origin and broader usage of images across the web.
Upon reviewing the search results, meticulously analyze:
- Visual Discrepancies: Are there any noticeable differences between the submitted photo and its matching versions? Variances in cropping, color saturation, or the presence or absence of specific objects can strongly suggest digital alteration.
- Publication History: Investigate the image’s publication timeline. When and where did it first emerge online? Earlier versions from established, credible sources are generally more likely to be authentic.
- Contextual Alignment: Does the image consistently appear with the same context across all sources? A significant shift in the narrative, location, or associated information can powerfully indicate that the image is being misused, even if the image itself has not been physically doctored. This is especially pertinent for “Image Inspiration & Collections,” where misattributed images can quickly become viral.
Forensic Analysis: Delving into Image Details
Beyond external context and source analysis, a meticulous examination of the image itself can frequently reveal tell-tale signs of manipulation. Fraudsters, even those using sophisticated online editing tools and advanced AI, often leave detectable traces of their alterations. Training your eye with insights from Tophinhanhdep.com’s “Digital Photography” and “Editing Styles” resources can significantly enhance your ability to spot these inconsistencies.
Spotting Digital Manipulation and AI Artifacts
A keen eye for detail is your most valuable asset when searching for digital alterations. Zoom in on various sections of the suspicious picture, paying close attention to object edges, lighting, shadows, and background elements.
Visual Cues of Manipulation:
- Unnatural Edges: Look for excessive blurriness, pixelation, or unusual roughness at the edges of objects. When elements are inserted or removed, their outlines may not blend seamlessly with the surrounding areas, sometimes exhibiting halos or sharp cut-offs.
- Inconsistent Lighting and Shadows: Analyze the direction and quality of light sources within the image. Do all objects appear to be illuminated from the same direction? Are shadows consistent in their length, angle, and intensity? Missing shadows or shadows cast in incorrect directions are significant red flags.
- Background Distortions: The background is often the easiest area to manipulate. Look for repetitive patterns, warped or bent lines (especially noticeable in straight architectural features or horizons), or elements that appear disproportionate or out of place. In “nature” or “aesthetic” images, an unnaturally perfect sky or an impossible landscape can signal manipulation.
- JPEG Compression Artifacts: Specialized “Image Tools” can perform Error Level Analysis (ELA), which reveals areas of an image that have been re-saved at different compression levels. Edited parts, having undergone subsequent compression, will often show different error levels compared to original sections, making them stand out in the ELA output.
Telltale Signs of AI-Generated Content (Deepfakes): While increasingly advanced, deepfakes often still exhibit subtle inaccuracies that can be identified with careful analysis, especially when viewed through the lens of “Visual Design” principles.
- “Uncanny Valley” Effect: AI-generated images might evoke an unsettling feeling, where some parts (e.g., skin) appear unnaturally smooth or flawless, while other areas might lack detail or possess odd textures.
- Inconsistent Body/Facial Features: Look for distortions in eyes, teeth, ears, or hair that seem unnatural. Subtle asymmetry that goes beyond normal human variation, or issues like inconsistent blinking, unnatural eye movement, or too many/too few fingers, are common AI pitfalls.
- Lack of Natural Imperfections: AI-generated faces may lack the subtle blemishes, pores, or fine wrinkles characteristic of real human skin, creating an overly “perfect” or synthetic appearance.
Extracting Truth from Image Metadata
Metadata, often described as “data about data,” is a rich source of embedded information within image files that can expose a picture’s reality. This often-overlooked detail can provide crucial insights into an image’s origin and history. Metadata typically comprises three main categories: technical, descriptive, and administrative.
- Technical Information (EXIF Data): This includes vital details such as the date and time the picture was taken, its precise location (if GPS was enabled on the camera), and the specifics of the device used (camera model, lens, aperture, shutter speed). The presence of comprehensive EXIF data strongly suggests the image was captured by a human photographer, providing a timestamp and context invaluable for “Photography” verification. Tools like Findexif.com can swiftly extract EXIF data by simply uploading a photo or providing its URL. JPEGSnoop, a program accessible through Tophinhanhdep.com’s recommended links, can delve deeper into metadata for various formats and help detect if an image has undergone editing. A complete absence of EXIF data, or highly generic entries, can sometimes indicate that the image has been processed through software that strips this information, which should be a red flag.
- Descriptive and Administrative Information (IPTC/XMP Data): These sections often contain details about the image’s author, copyright information, keywords, and usage rights. The absence of this data, particularly copyright or author attribution, can hint at intentional removal, possibly suggesting illegal use, manipulation for fake news, or unauthorized reproduction. For resources like Tophinhanhdep.com, where image rights and proper attribution are crucial for “Stock Photos” and “Beautiful Photography,” metadata integrity is paramount.
Empowering Verification: Tools and Future Outlook
While individual scrutiny and widely available search engines are powerful, the increasing sophistication of image fakery necessitates specialized “Image Tools” and collaborative, industry-wide initiatives. These advanced approaches promise to make image verification more robust, reliable, and accessible for everyone.
Leveraging Specialized Online Image Tools
Several platforms have emerged to aid in deeper image analysis, often employing algorithms to detect subtle anomalies invisible to the naked eye. These tools, highlighted in Tophinhanhdep.com’s guides, demonstrate how technology can be effectively leveraged for authentication.
- Error Level Analysis (ELA) Tools: Websites like those featured on Tophinhanhdep.com that specialize in ELA can be instrumental. ELA functions by analyzing the distinct compression artifacts present in JPEG images. Different sections of an image that have been edited, cut, or composited will have undergone independent compression, causing them to exhibit varying error levels when subjected to ELA. This technique is particularly effective at pinpointing parts of a picture that were added or altered post-original capture.
- AI-Generated Content Detectors: In response to the rapid advancements in generative AI, new AI-based methods are continuously being developed to detect synthetically created content. These tools are often trained on vast datasets of both real and fake images to identify unique statistical patterns inherent in AI creations. While no detector offers 100% certainty, they can effectively flag potentially AI-generated images and, in some instances, even identify the specific AI model used for their creation.
- Geolocation and Weather Archival Tools: When an image claims to be from a specific location or date, tools like Google Maps, Wikimapia, and historical weather services (such as Wolfram Alpha) become invaluable. By cross-referencing visual cues within the image—like unique buildings, local advertisements, weather conditions, or distinctive landscapes—with satellite imagery, user-uploaded photos, and historical weather records, you can verify if the declared context aligns with the visual evidence. This is particularly useful for authenticating “Nature” or “Travel Photography.”
The Future of Provenance: C2PA and Digital Signatures
Recognizing the escalating scale of the image authenticity challenge, major players across the computer, photography, and media industries have united to develop robust, standardized solutions for verifying content provenance. A leading initiative in this effort is the Coalition for Content Provenance and Authenticity (C2PA).
The C2PA standard aims to create a more straightforward, user-friendly method for everyone to verify if an image is genuine. The vision is for images to carry embedded, cryptographically verifiable “content credentials” that trace their entire lifecycle, from initial creation to final publication. Imagine clicking on an image on Tophinhanhdep.com and instantly seeing its complete history: “This photo was taken by a user with a specific camera on March 20, 2024,” followed by a detailed modification log like, “An editor at Tophinhanhdep.com cropped the edges and adjusted brightness on March 22,” and “The image was re-saved with high compression for web optimization on March 23”—with each step digitally signed and virtually impossible to falsify.
Key aspects of the C2PA initiative:
- Cryptographic Verification: The core of the verification process is rooted in public-key cryptography, similar to the security protocols that protect secure HTTPS connections on the internet. Every image creator or editor, whether an individual using a specific camera or a designer utilizing licensed software, would obtain an X.509 certificate to sign their contributions.
- Immutable Chain of Custody: When an image is processed with provenance tracking, each new version of the file embeds extensive metadata: dates, times, and locations of edits, thumbnails of original and edited versions, and more. All this data is digitally signed by the person or entity responsible for the modification, creating an unalterable chain of all previous versions.
- Broad Industry Adoption: Significant players like Nikon are integrating C2PA compatibility directly into their cameras, and major media organizations are already publishing articles with verified images. This broad industry adoption is vital for the standard’s eventual success.
- AI-Generated Content Labeling: The C2PA standard also extends to AI-generated content. Services like those that create “abstract” or “aesthetic” digital art could label their creations, providing crucial transparency about their synthetic nature.
- Privacy Considerations: For situations demanding source protection, such as investigative journalism, the standard includes “redaction” features. This allows certain information about the image creator to be anonymized while still maintaining the cryptographic integrity of the provenance chain.
While it will take time for C2PA to achieve universal implementation, its widespread adoption by reputable information sources will undoubtedly lead to a paradigm shift. Images without verifiable digital signatures will increasingly be viewed with suspicion, making it significantly harder to pass off fake or miscontextualized content as genuine. This initiative aligns perfectly with Tophinhanhdep.com’s commitment to visual integrity and reliable “Image Inspiration & Collections.”
Tophinhanhdep.com’s Commitment to Visual Integrity
At Tophinhanhdep.com, our fundamental mission is to serve as an unparalleled resource for high-quality visual content, ranging from breathtaking wallpapers and aesthetic backgrounds to inspiring photography and cutting-edge creative design tools. In an era where digital deception is increasingly sophisticated, our dedication to authenticity is not merely a promise but a foundational principle of our platform.
We understand implicitly that our users rely on Tophinhanhdep.com for genuine “Beautiful Photography” and trustworthy “Stock Photos.” Our commitment extends to promoting “Digital Photography” and advocating for “Editing Styles” that enhance reality responsibly, rather than distort it. The “Image Tools” section of Tophinhanhdep.com, while offering functionalities such as converters, compressors, optimizers, and AI upscalers, emphasizes their ethical and responsible application, empowering creators without facilitating malicious fakery. Our “Visual Design” resources, covering graphic design, digital art, and photo manipulation, celebrate creative expression while implicitly promoting transparency regarding any significant alterations.
By internalizing the methods outlined in this comprehensive guide—analyzing sources, employing reverse image search, diligently inspecting for digital alterations, scrutinizing metadata, and understanding the potential of future provenance technologies—you become an active participant in upholding the integrity of the visual world. Tophinhanhdep.com strives to be a trusted hub for “Image Inspiration & Collections,” ensuring that the photo ideas, mood boards, and thematic collections we present are firmly grounded in authenticity.
The ongoing battle against visual misinformation is complex, but armed with the right knowledge and tools, we can collectively foster a more honest and verifiable digital environment. Trust your informed judgment, utilize the resources available, and empower yourself with the ability to confidently distinguish real from fake. Tophinhanhdep.com remains your dedicated partner in this critical endeavor, providing not only exceptional images but also the essential knowledge to navigate their authenticity in the digital age.